When I started integrating Zapier with our platform, I quickly ran into a familiar problem for many developers Zapier expects OAuth 2.0, but our platform uses a different authentication model.
Our authentication stack was built on JWT. It worked perfectly for internal APIs, but it didn’t fit the OAuth handshake for Zapier. Go to my other blog regarding Integrating Zapier
That’s when I discovered OryHydra, and it became a perfect match and the most important component of our ecosystem.
Problem
OAuth looks simple: redirect users to authorize, exchange tokens, and use the token to get access, but it’s more involved when you start building; a lot is hiding under the hood:
- Handling access and refresh tokens
- Securing Redirect URLs
- Managing client credentials
- Issuing scoped access
- Storing and validating tokens safely
I wanted something that gave me all of this without writing my own OAuth server or compromising our existing JWT-based flow.
Why I Chose Ory Hydra?
Ory Hydra is an Open-Source OAuth 2.0 and OpenID Connect provider to secure APIs. It doesn’t handle user login directly. Instead, it delegates login and consent to your existing login flow.
That design actually fits in our case. We don’t want to create another login page that can be handled for Zapier and our regular login flow for our Application.
Here is why it actually fits:
First: It adds OAuth support without replacing our existing JWT-based authentication
Hydra works alongside our existing JWT-based authentication system. It issues OAuth 2.0 access tokens for third-party applications like Zapier, while our backend continues to use JWTs for authenticating our own users.
This meant I didn’t need to rewrite our existing authentication logic — I only added an OAuth-compatible authorization layer for external integrations.
Second: Open Source
Hydra is built on open standards and is fully open source. You can run it locally, inspect the code, and integrate it with your own identity logic. There is no billing for using an open source platform; just a AWS EC2 billing to host on the server. Ory also provides a managed cloud service (Ory Network) and related components such as Ory Kratos for identity management. In our case, we chose the open-source Hydra deployment so we could keep full control over our existing login and consent flows.
As I want to use our login ecosystem, I chose to go with open source, hosting on our server.
Third: Integrates Easily
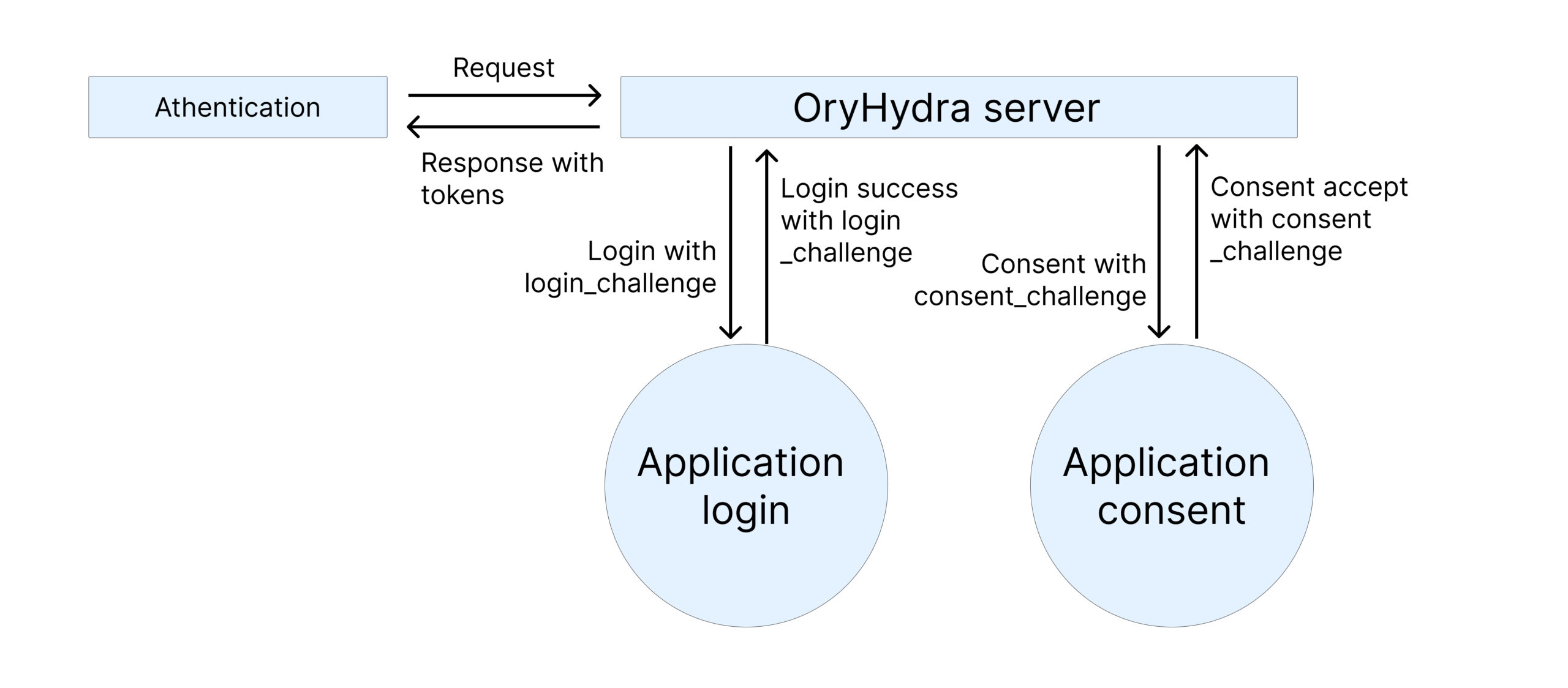
Hydra is agnostic to how you implement user authentication. It only requires you to provide endpoints for login and consent, which can be backed by your existing authentication system. It just asks: “Where should I send users to log in?” and “Where should I get consent from?”
I need to set these two links in the Ory Hydra configuration so when our application user tries to login, Ory Hydra redirects to the login page and follows to the consent page.
Diagram to understand:
Comparison with Keycloak OAuth Solution
I started with Keycloak first before going with OryHydra. Then I got to know about OryHydra. After going through both ecosystems, design, and user management, I decided to move forward with OryHydra as per my requirements.
| Capability | Keycloak | Ory Hydra |
|---|---|---|
| OAuth2 / OIDC provider | ✅ Yes | ✅ Yes |
| Custom login UI | ❌ Included (You need to use keycloak’s user login page) | ✅ You can provide your own login page |
| Custom consent UI | ❌ Included (You need to use keycloak’s user consent page) | ✅ You can provide your own consent page |
| Works with existing user database | ⚠️ Possible but needs integration/federation | ✅ Native approach |
| Keeps your current auth logic | ❌ Typically replaced or adapted | ✅ Fully preserved |
| Flexibility with custom auth flows | ⚠️ Moderate | ✅ High |
| Best fit | All-in-one IAM | OAuth server for existing auth systems |
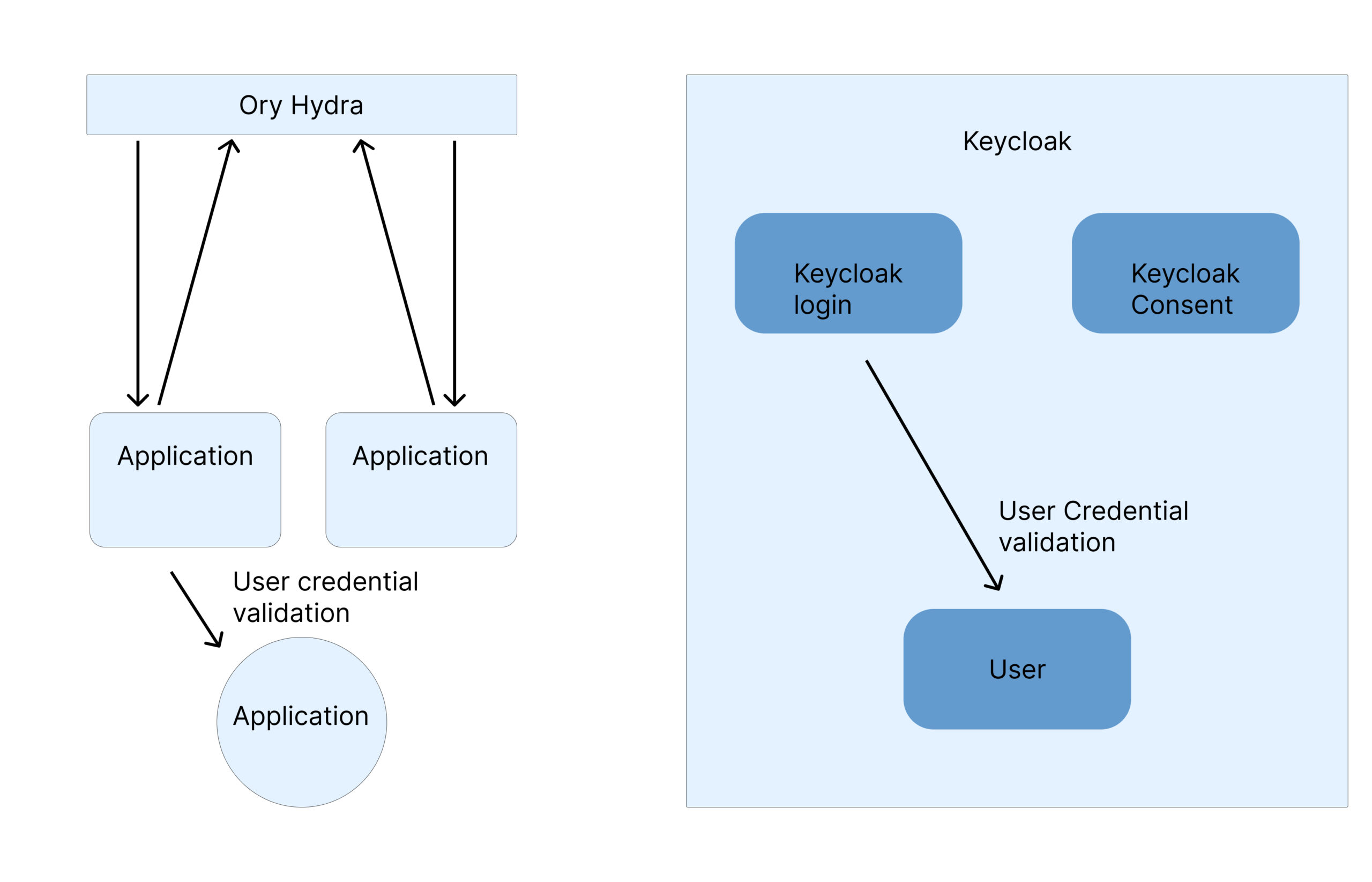
Keycloak and Ory Hydra are both open source OAuth providers, but different in some cases:
- Keycloak has its own login and consent page, whereas in Ory Hydra, you just need to configure your own login consent URLs
- Keycloak includes its own user management system and built-in login UI, which often requires integrating or migrating your existing user store into the Keycloak ecosystem.
- With Ory Hydra, you can continue using your existing user database and authentication loci, because Hydra delegates login and consent handling to your application.
Takeaways for the Developers considering Hydra
- It’s not plug and play for non-technical teams; you need to understand the OAuth flow (login + consent + Redirect URLs endpoints)
- Hydra doesn’t manage users; it integrates with what you already have. You can show your login UI and consent UI.
- Hydra’s config is strict, especially for redirect URIs and token URLs. So you have to make sure that the configuration is correct in production.
- Official Hydra’s Docker images make Hydra setup painless.
About the Author ✍️
Rushit Padia — Developer Lead | Full Stack Engineer
Building tools that automate workflows and save hours for service businesses. LinkedIn

